Authorization
Salla App Store.
All calls to the Merchant Public APIs require an Authorization header in this format:
Authorization: Bearer
<ACCESS_TOKEN>What You will Need Before You Start:
First Step
Open and verify account on Salla Partners.
Second Step
Either use a sample App you created previously or build a new one from the scratch.
Third Step
Choose an OAuth method, Easy Mode or Custom Mode Authorization.
Fourth Step
Set up the scopes of your App to specify the needed access level.
Fifth Step
Generate a demo store, so no sensitive data is compromised.
Sixth Step
Install the App on the demo store for real-world mockup test.
Salla OAuth Benefits
🔐 Authorized Access
Apps are given authorized access, which means they can only access resources that the Merchant has authenticated.Salla’s OAuth2.0 Flow
The authorization Flow
| URL | Description |
|---|---|
| Authorization Endpoint | https://accounts.salla.sa/oauth2/auth This URL initiates the process of obtaining the merchant's permission for the App to access their store data on Salla. |
| Token Endpoint | https://accounts.salla.sa/oauth2/token After the merchant grants permission, the App exchanges the authorization code for an access token at this endpoint. |
| Redirect URI | https://client-app.com/callback Once the authentication process is complete, the authorization server redirects the user's browser to the registered redirect URI. |
| Refresh Token Endpoint | https://accounts.salla.sa/oauth2/token If a refresh token is granted, this endpoint allows the client to obtain a new access token when the current one expires. |
| User Info Endpoint | https://accounts.salla.sa/oauth2/user/info Once the authentication process is completed successfully, the Merchant details can be received via this endpoint. |
| Query Parameter | Description | Example |
|---|---|---|
client_id | Identifies the client application making the request, which values can be fetched from your application on the Salla Partners Portal. | 1311508470xxx |
client_secret | Identifies the client application making the request, which values can be fetched from your application on the Salla Partners Portal. | 362985662xxx |
response_type | Specifies the desired response type from the authorization server. | code |
redirect_uri | Indicates the URI for user redirection after completing the authorization process. | https://your-app.com/callback-url |
scope | Specifies the requested permissions or access levels. | offline_access |
state | Used to maintain state between the authorization request and the callback to prevent cross-site request forgery attacks. | 1234xxxx |
code | The authorization code returned by the authorization endpoint. | xxxxxxxx |
grant_type | Specifies the type of grant being used to authenticate the client. | authorization_code |
Including the client ID as a query parameter
https://accounts.salla.sa/oauth2/auth?client_id=your_client_id&response_type=code&redirect_uri=https://client-app.com/callback&scope=read write&state=random_valueclient_id=your_client_id is appended to the authorization URL, where your_client_id should be replaced with the actual client ID issued by the authorization server.The installation URL
app-id as a parameter. This URL can be used to initiate the app installation process. When the merchant clicks on the installation URL, the App will be automatically installed into their Salla Store.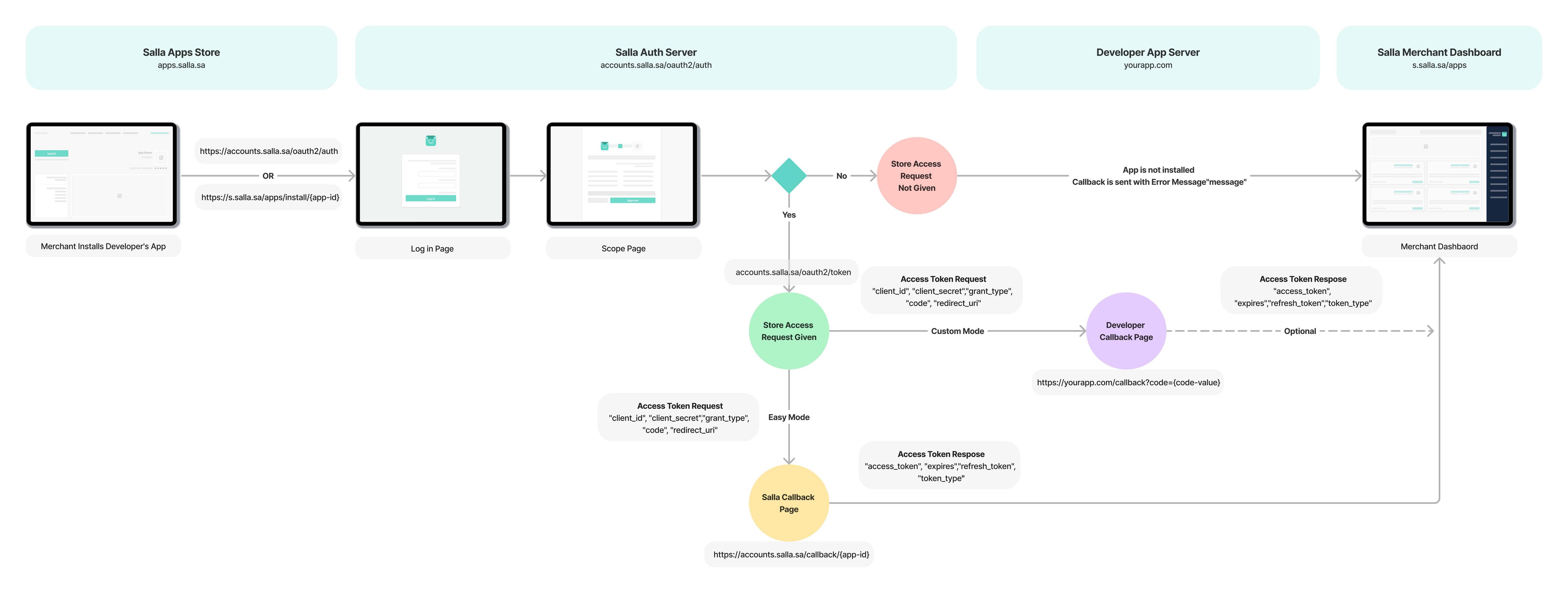
Types of OAuth 2.0 in Salla

Easy Mode (Recommended)
app.store.authorize, and then the process of generating the “access token” will be handled automatically at Salla‘s side back to you via the Webhook URL specified in the Webhooks/Notifications your of your App.Generate Access Token using Salla App and Demo Store
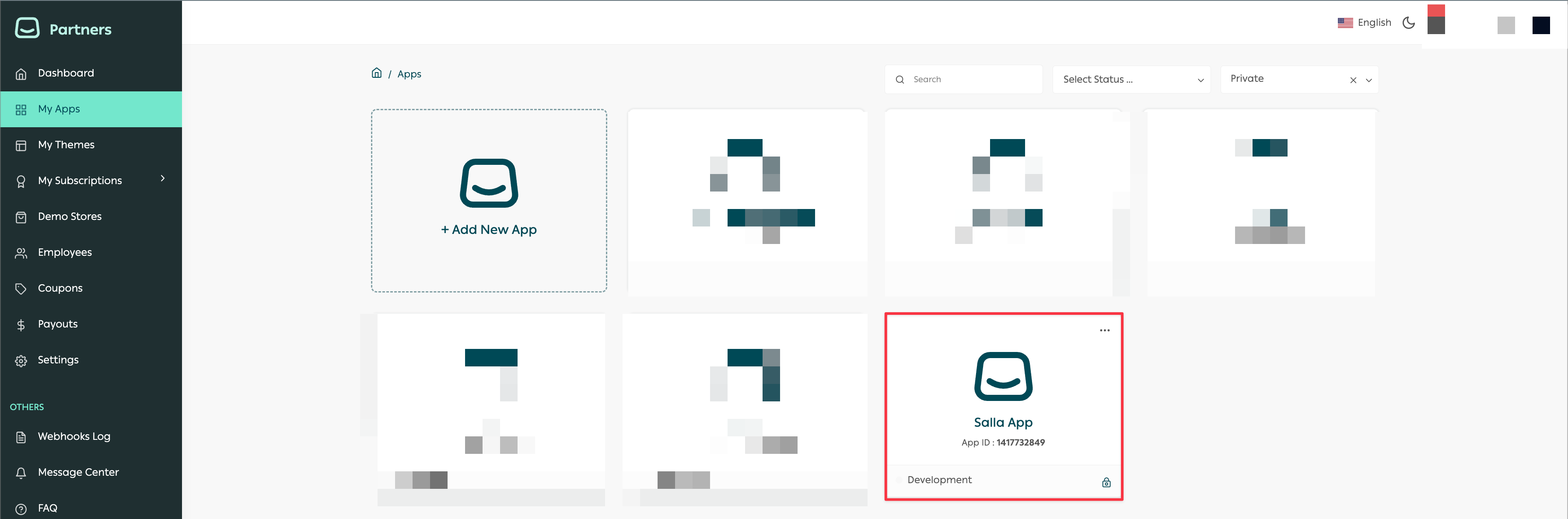
Salla Partners Dashboard | Application
On the Partners dashboard, go to Apps and choose any App you developed.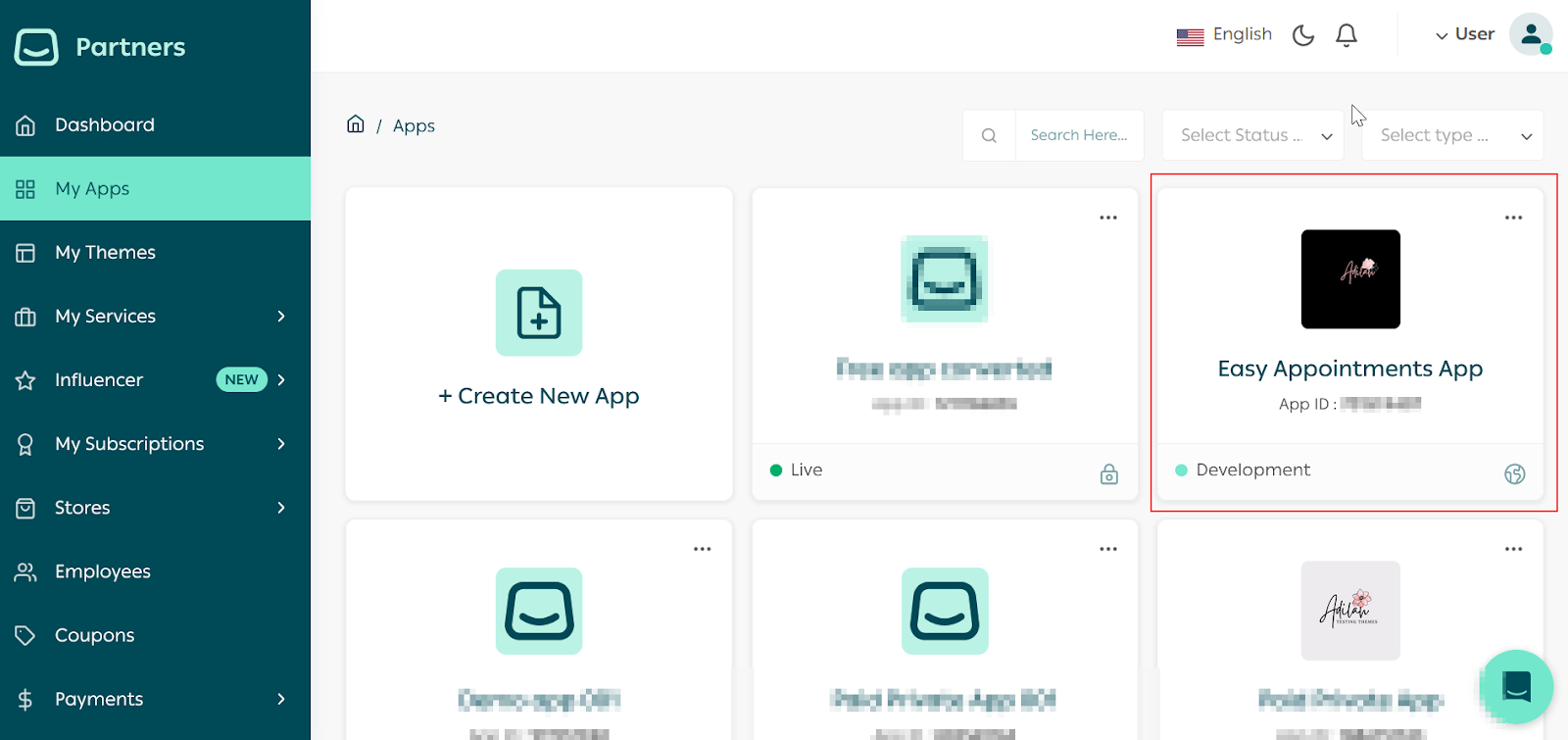
App Scopes Setup
Set up the App Scope and check the boxes that matches your app scope, such as Product, Order and Webhooks, then click Update Scope.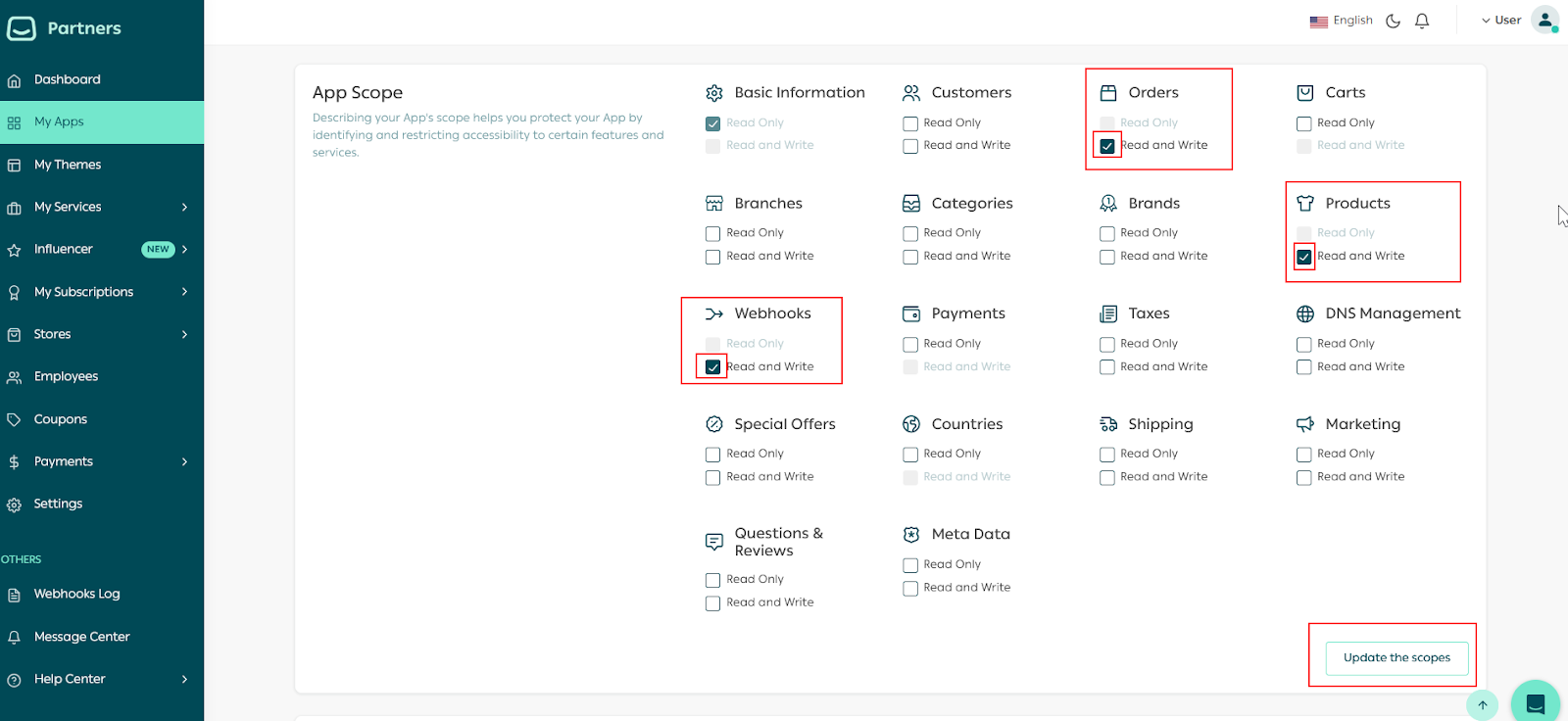
Webhook Setup
Set up the App Webhooks details using Webhook.site. Copy the Webhook link from the page.It is best to use your own webhook, since webhook.site is only for demonstration purposes. 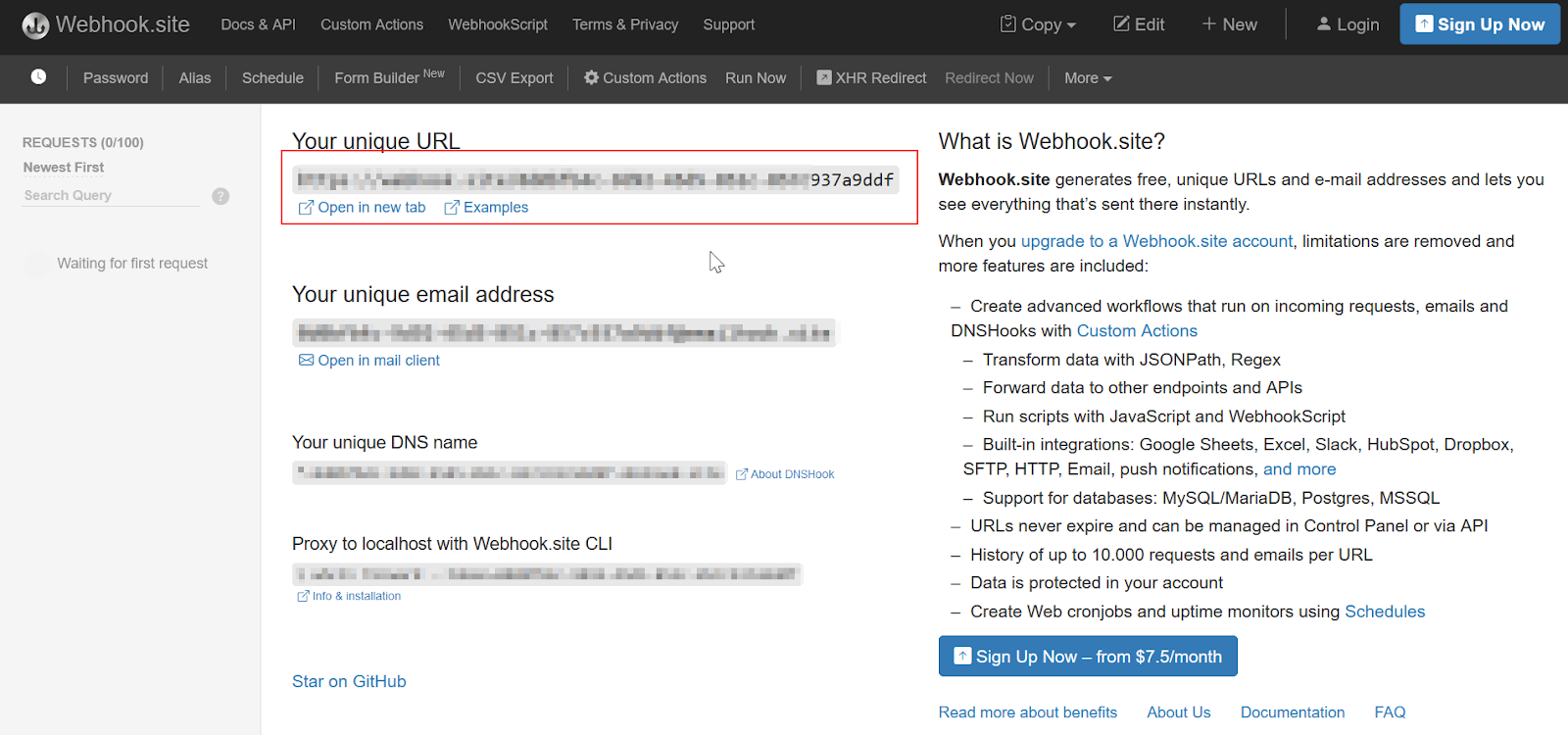
Add Webhook on Salla Partners
Then add it as a Webhook URL for the App.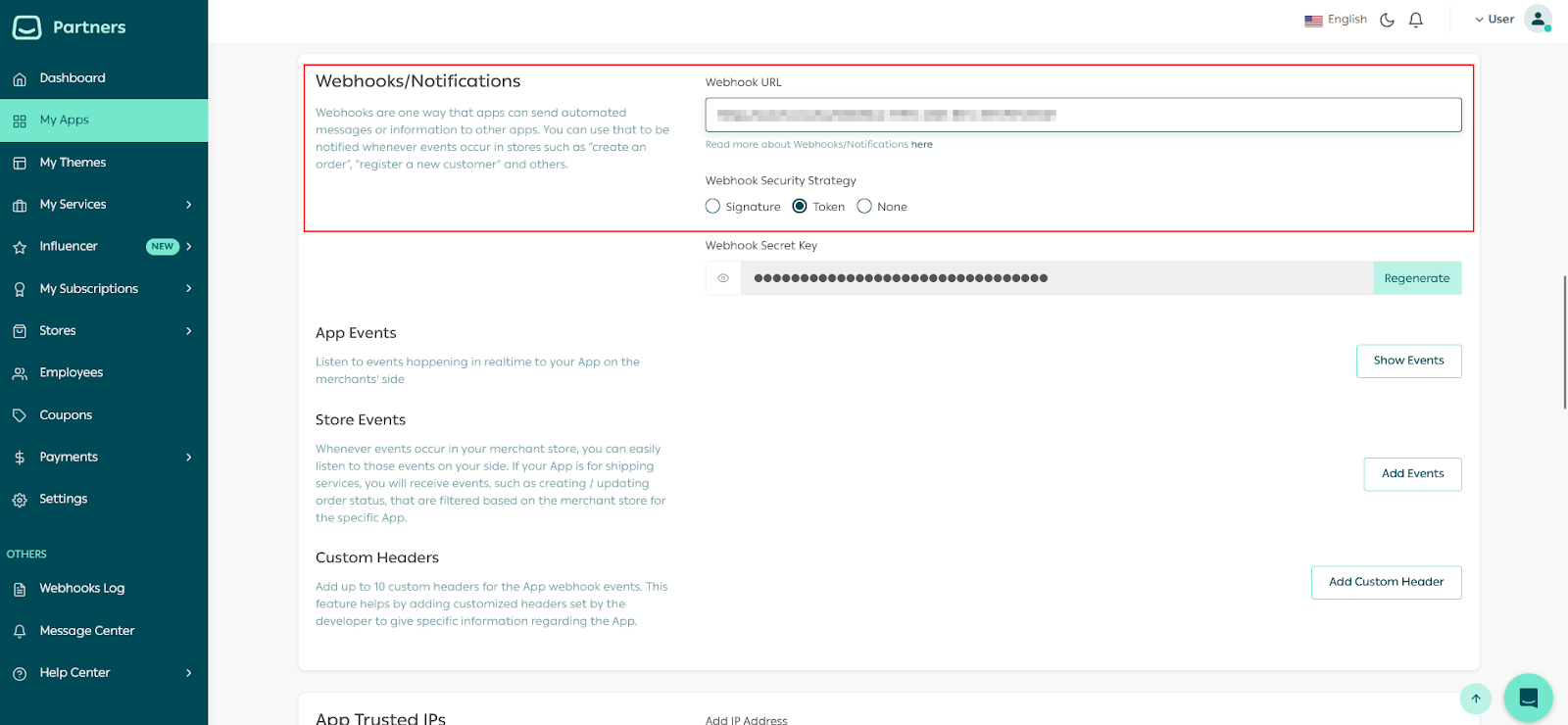
Install App using Demo Stores
Scroll down to the Test App section and install the App on a demo store by clicking the Install App button next to the demo store.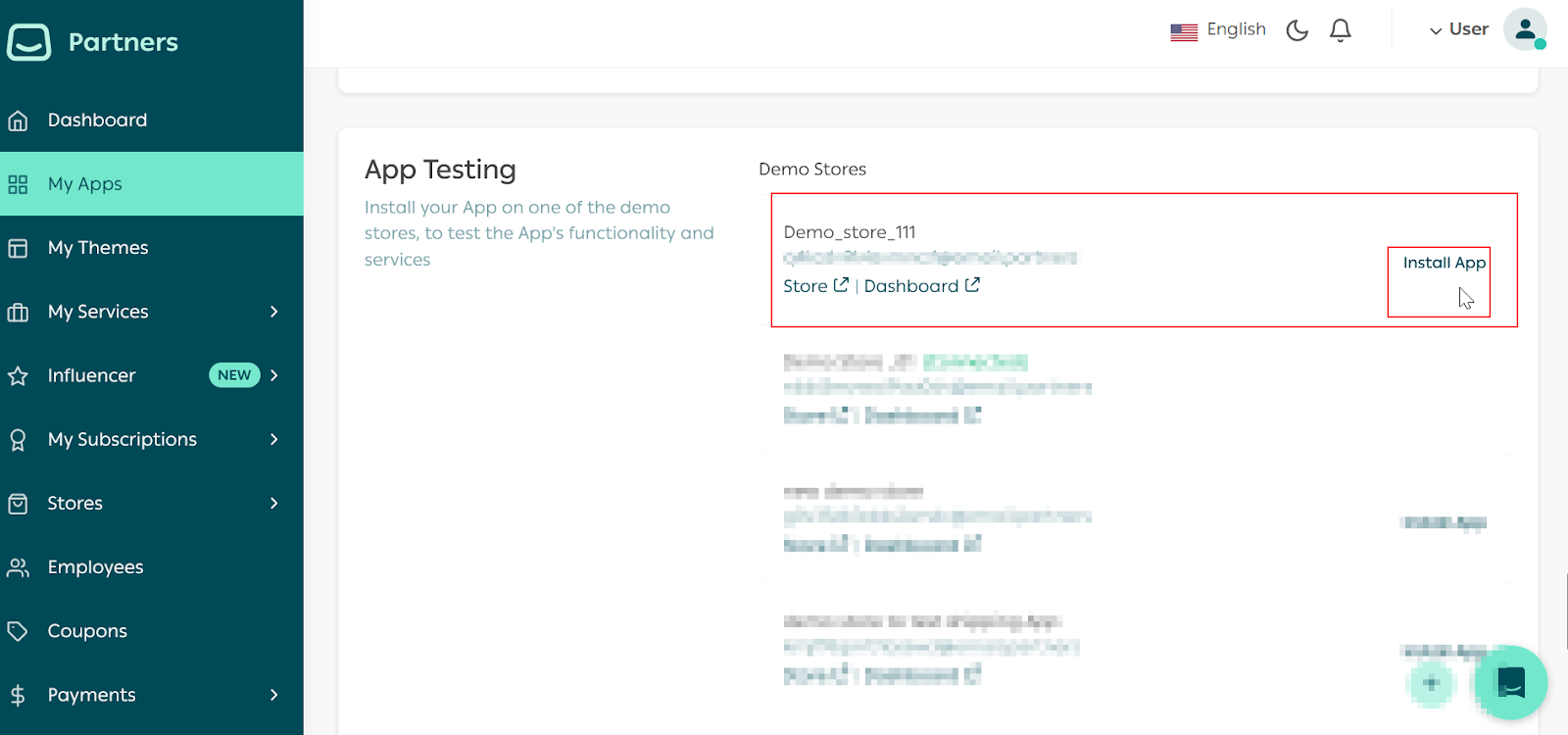
App Approval as a Store Owner
This will redirect you to the store dashboard page where you can approve the App installment. Approve the installment request to proceed.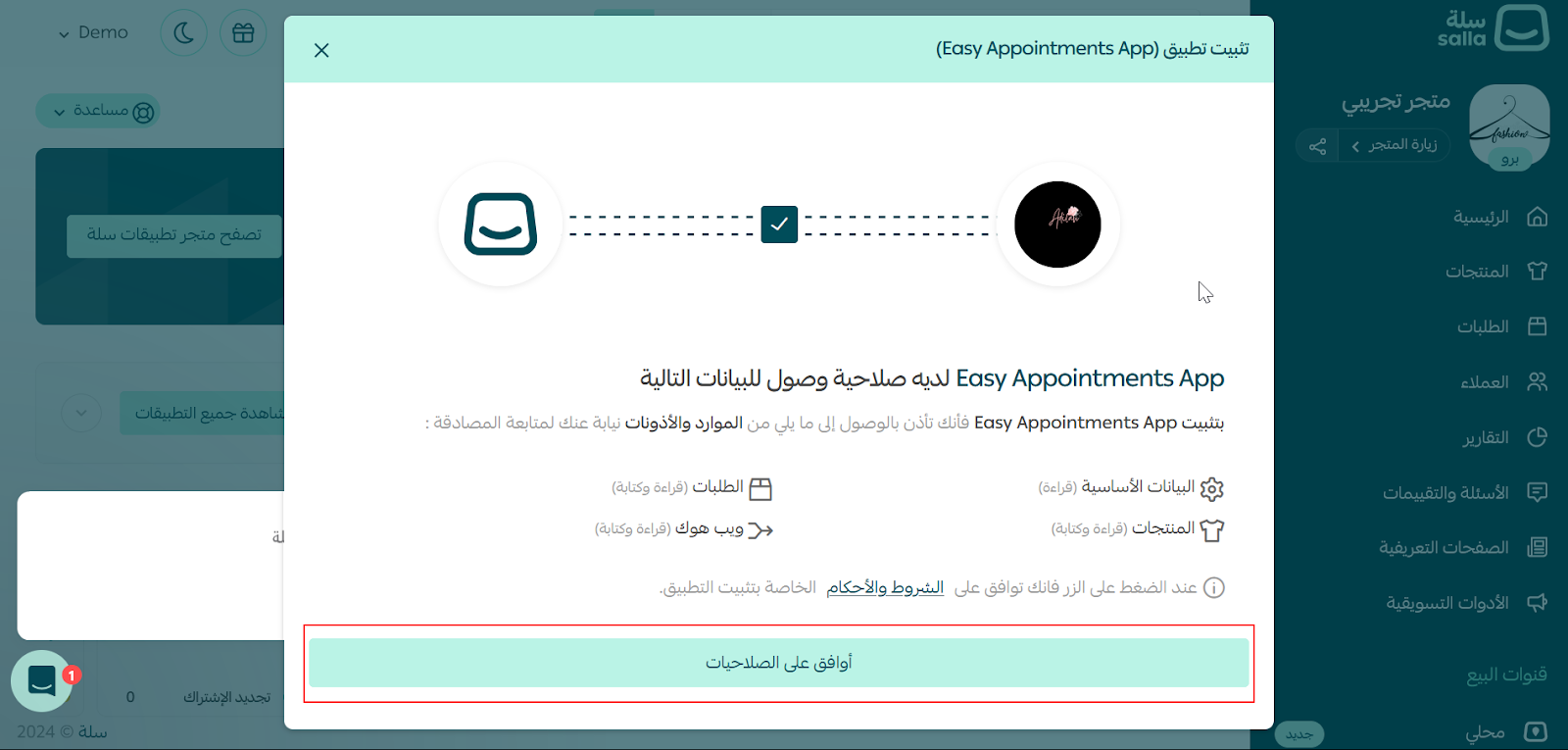
Retrieve Access Token from Webhook
After that, go back to the Webhook.site and get the Access Token from the 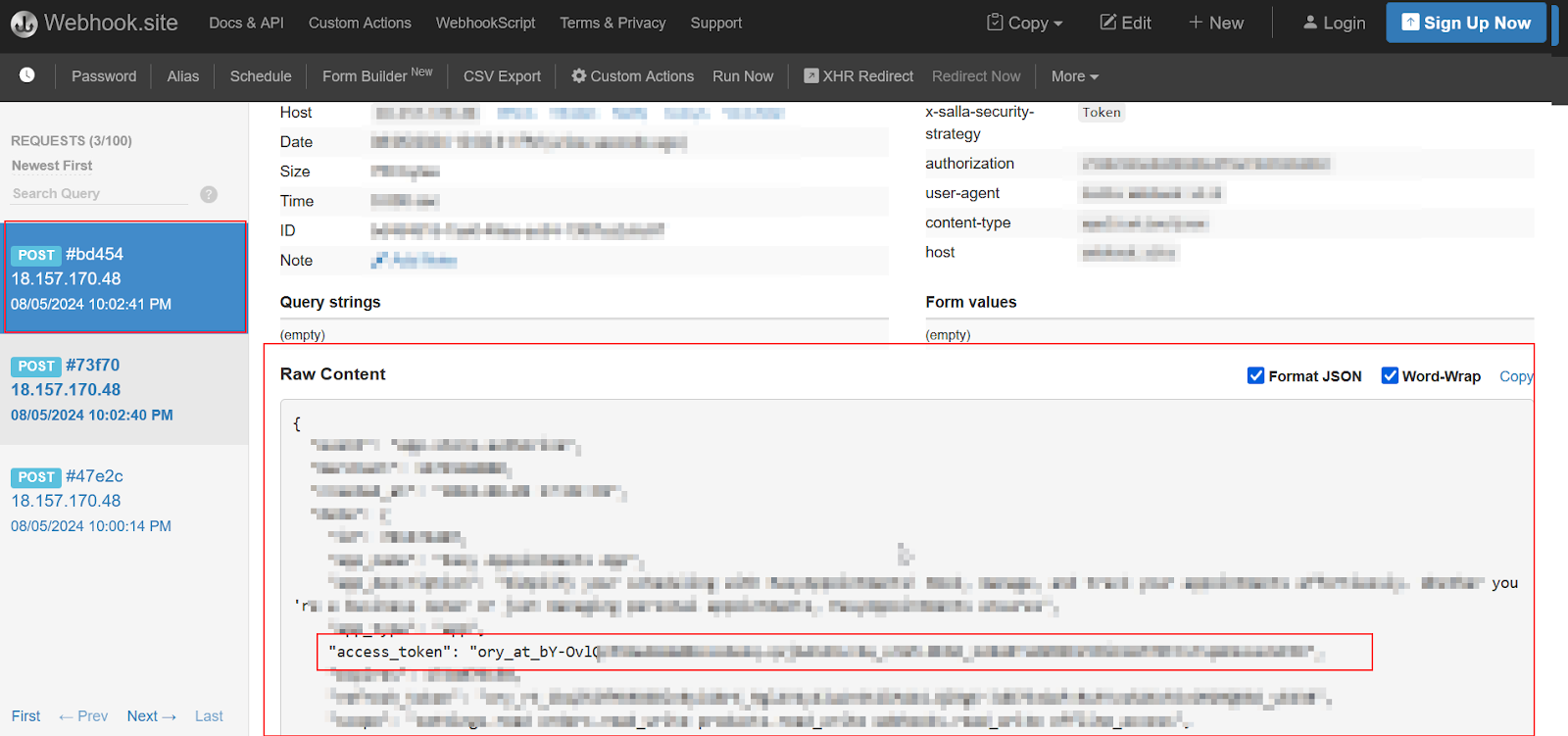
app.store.authorize event.App Update
app.updated event. After that, Salla sends you the app store.authorized event, which provides you with the new access token and refresh token. This information will be delivered to you via webhook. Accordingly, you are required to update the access token and refresh token in your database.WARNING
expires variable is returned as a unix timestamp value for the app event app.store.authorize.Custom Mode
Custom Mode Use Cases:
App for online grocery stores that redirect users back to the store after they log in with their Google account.
1. User Authorization
Once the Merchant has logged in to their Salla Store account, they will be prompted by Salla to authorize access to your App. The merchant will be asked to grant authorization for your App to access their store data with the defined scopes.
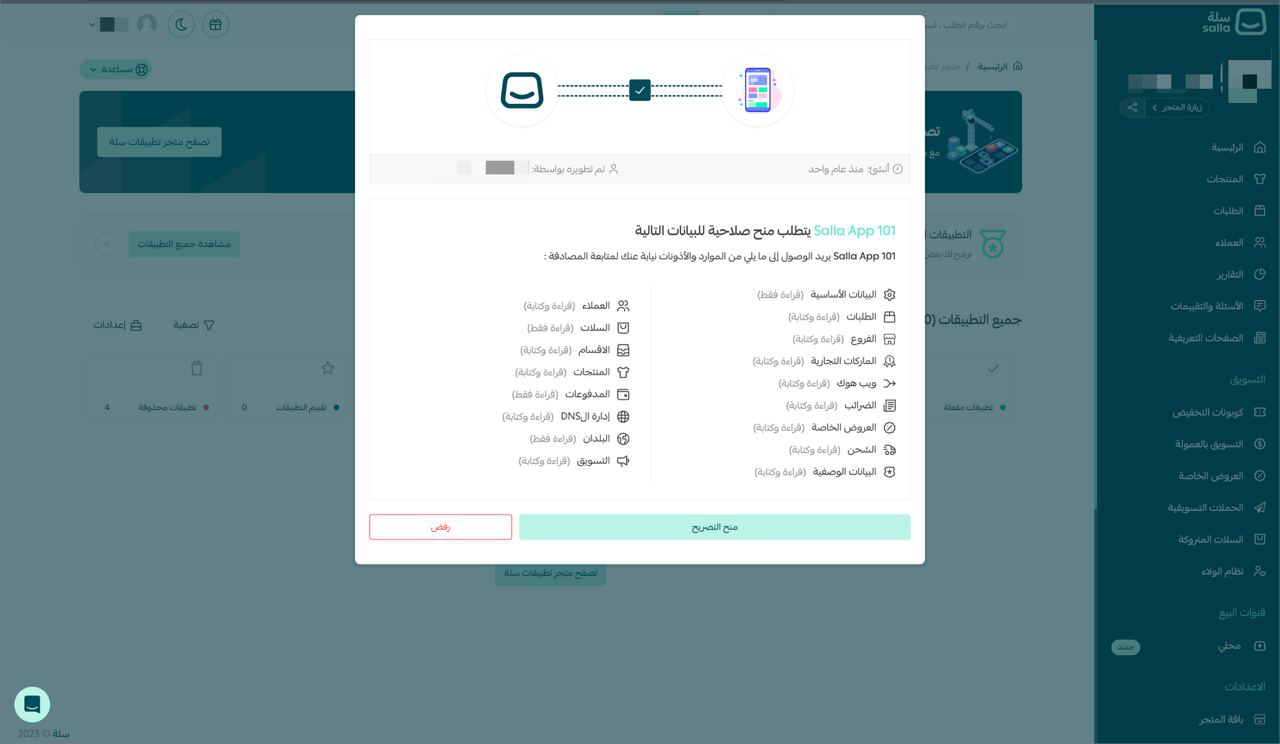
https://yourapp.com/callback?code={code-value}&scope={app-scopes}+offline_access&state={state-value}
2. Access Token Generation
POST request with the required parameters to the token endpoint.Access Token Request
Access Token Response
Easily run the request straight from Postman by providing the required data to generate an access token

Easy Mode is the only way allowed for published apps on the Salla App Store. Since Postman uses custom mode, you can implement that in your app for testing purposes only.
WARNING
Body Definition
AccessToken
Important Notes
| • Access tokens expire after 2 weeks (14 days). |
• If you want to generate the refresh token, set the scope value as offline_access. E.G: scope = offline_access. |
• The expires variable is returned as seconds timestamp value |
• Upon obtaining the access token, developers can utilize the User Info endpoint URL, https://accounts.salla.sa/oauth2/user/info, to retrieve the Merchant details and store them alongside the access tokens. |
Refresh Access Token
Warning: Refresh Token Reuse
Recommended Implementation: To prevent refresh token reuse in your application, implement a mutex/locking mechanism for token refresh operations
Body Definition
Important Notes
Access Token Usage Example
IP Whitelisting
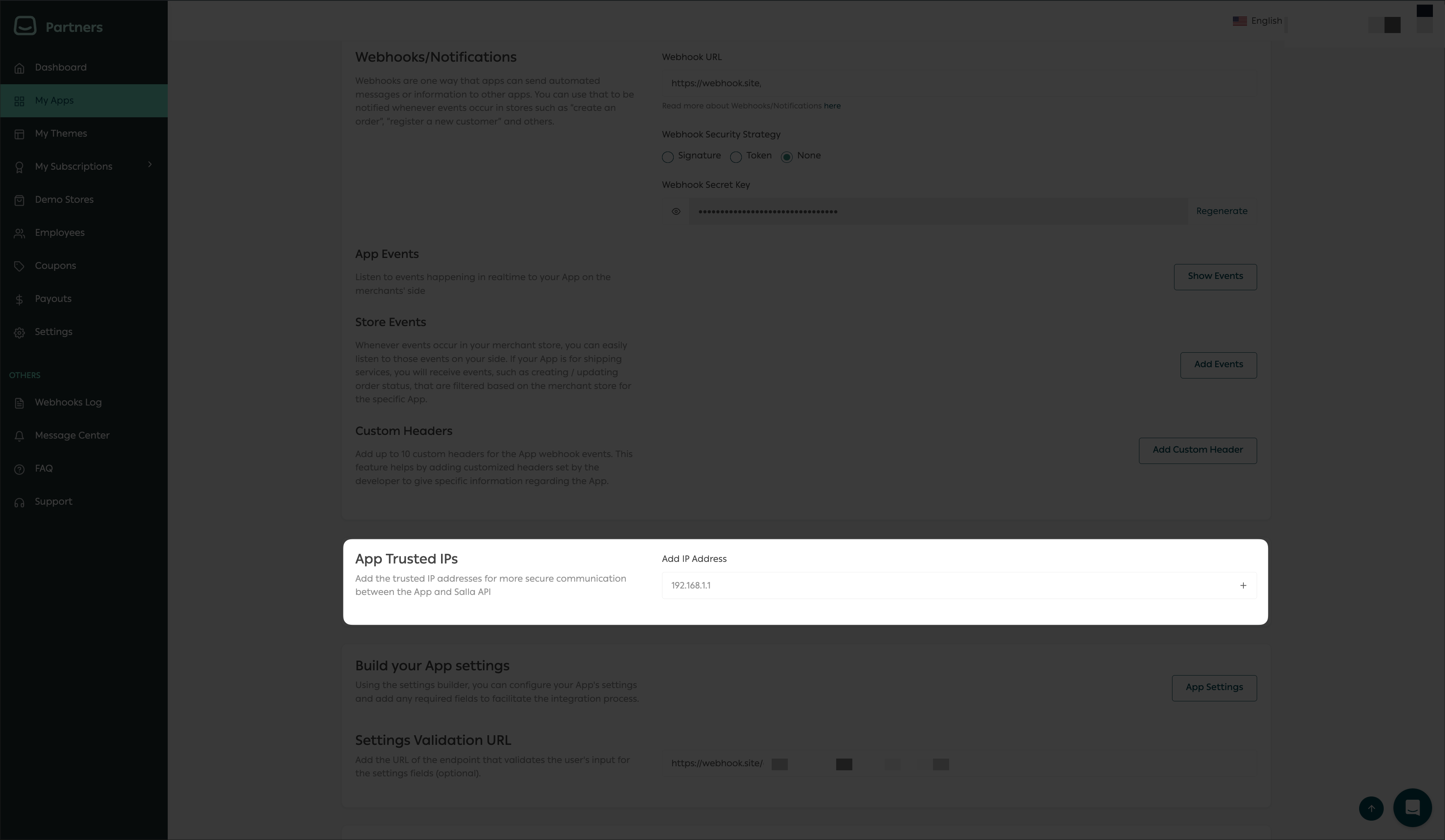
NOTE
Open-Source Libraries
Modified at 2025-09-17 10:51:58
